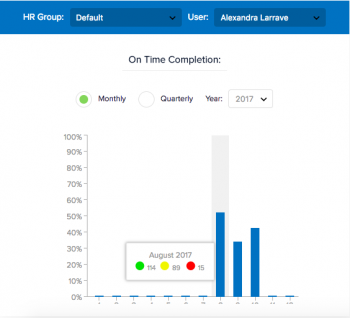
Why do some of your employees get all tasks done on time and as expected, but others can’t seem to have the same success rate, even when those tasks are critical and are designed to avoid, transfer, or reduce risks to the business?
Is it their motivation? Their DNA? Is it compensation? Is it culture?
Insights: IT Security
In the wake of the UK Parliament’s recent network security attack, it’s clear that no matter how well-designed our IT security systems and internal controls are, there’s always a risk of your organization falling victim to a cyber threat.
Deciding to implement a comprehensive information security framework like ISO 27001 or COBIT is not a trivial thing. These frameworks are comprehensive, cross-functional, broad reaching, and culture-changing. Here are 3 compliance software tools to help you through the process.
Why do some of your employees get all tasks done on time and as expected, but others can’t seem to have the same success rate, even when those tasks are critical and are designed to avoid, transfer, or reduce risks to the business?
Is it their motivation? Their DNA? Is it compensation? Is it culture?
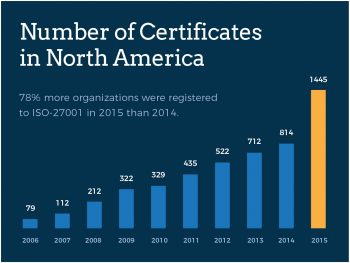
We dived deep into how companies set up Information Security Management Systems (ISMS) and found 8 key trends that lead to a successful ISO-27001 certification.
Corporations are constantly threatened by information security breaches. Learn how to effectively execute a comprehensive information security strategy.
CommandHound has worked with clients in a variety of industries who deal with sensitive information on a daily basis.
Headache-causing. Frustrating. Sluggish. These are some of the terms that go through our heads when trying to decode the complex regulatory requirements of Sarbanes-Oxley (SOX).
It looks like the European Union’s new GDPR will go into effect on May 25, 2018. Companies that fail to comply with its rules and regulations will face fines of up to $20 million euros (or 4% of sales for the preceding year). This is definitely not a trivial update.
Cyber security seems like a very complex issue that requires deep, and seldom available, expertise to do it right. Here is a quick checklist that our information security users have turned into a Template in CommandHound for others to use. This checklist goes after the low hanging fruit by applying the 80/20 rule.